We are proud to announce that the January 2022 release of KUY.io Konnect™ access server is now generally available to all customers.
This release includes an exciting new feature: support for different traffic policies including custom split-tunneling, as well as bug fixes and security updates!
Traffic Policies
Route All Traffic through KUY.io Konnect™
The default traffic policy in KUY.io Konnect™ access server sends all network traffic through the encrypted virtual private network (VPN) tunnel, regardless of destination. While this keeps all your traffic encrypted and protected, large file transfers and connections to certain business services like financial transaction services may prevent access through VPN networks, requiring you to disconnect your VPN connection to access those services.
Route VPN Traffic through KUY.io Konnect™ access server
With this traffic policy, only network traffic for addresses and devices that are part of the KUY.io Konnect™ VPN network block (configured during initial setup or via server settings) is routed through the virtual private network (VPN) tunnel. All other traffic is send through your open network.
Custom Split Tunneling
Split tunneling is a VPN feature that divides your network traffic and sends some of it through an encrypted virtual private network (VPN) tunnel, but routes the rest through a separate tunnel on the open network. Typically, split tunneling will let you choose which apps to secure and which can connect normally.
Split tunneling is a useful feature when you need to keep some of your traffic private, while still maintaining access to local network devices. So you can access foreign networks and local networks at the same time. It's also great if you want to save some bandwidth.
It lets you access more than one network at the same time, so you can get onto your corporate network or a foreign network while also remaining connected to your local network. This means you don’t have to keep connecting and disconnecting your VPN.
Server Default Policy
Administrator can set a default traffic policy to be applied to all newly created devices. To set a default traffic policy, log in to your KUY.io Konnect™ access server admin portal, and navigate to Settings / Server Settings. Set your desired traffic policy and click on Save.
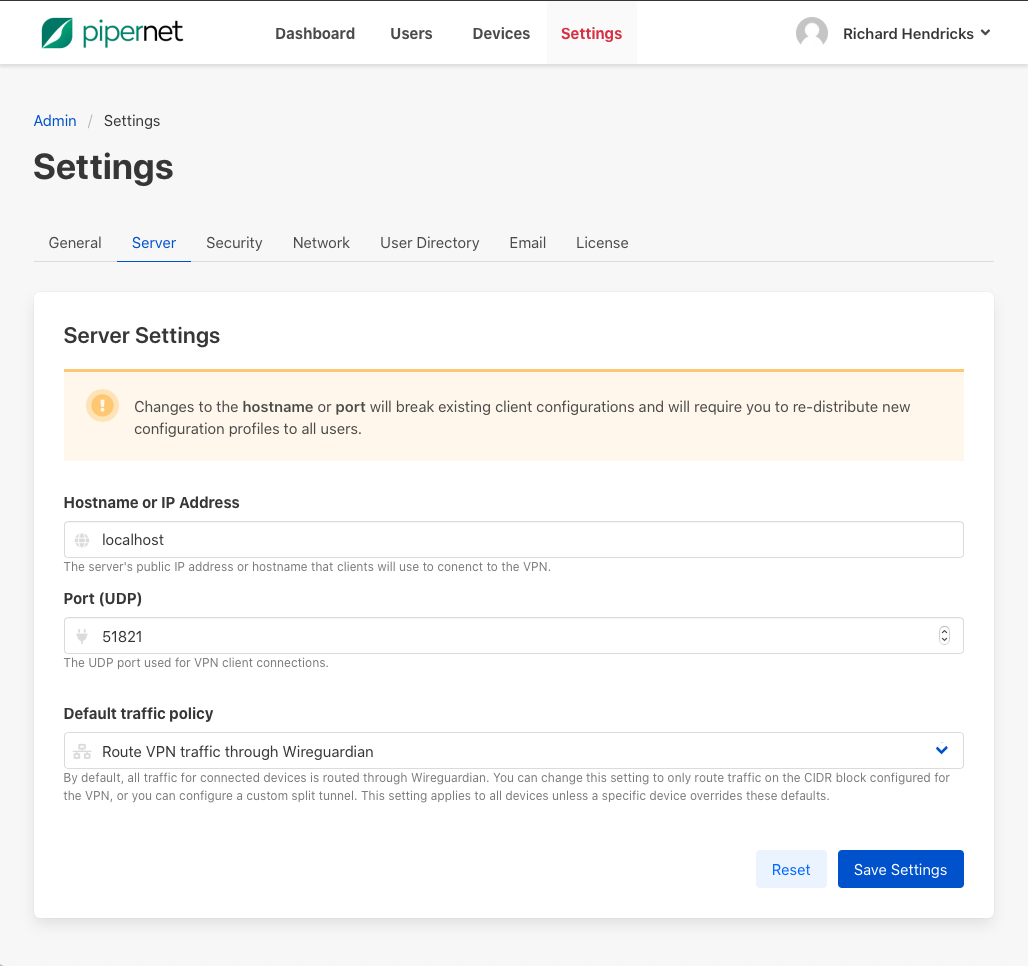
Administrators can set a server-default traffic policy that will be applied to all newly created devices
Per-Device Policy Overrides
Some devices, such as privileged or secured edge access devices may require custom traffic policies. Administrator can override the server-default traffic policy on a per-device basis. To apply a custom traffic policy for a specific device, log in to your KUY.io Konnect™ access server admin portal, and find the device that you wish to configure. Click on Edit Device and enable the Override default traffic rules switch. Select and configure your desired traffic policy for that device and click on Save.
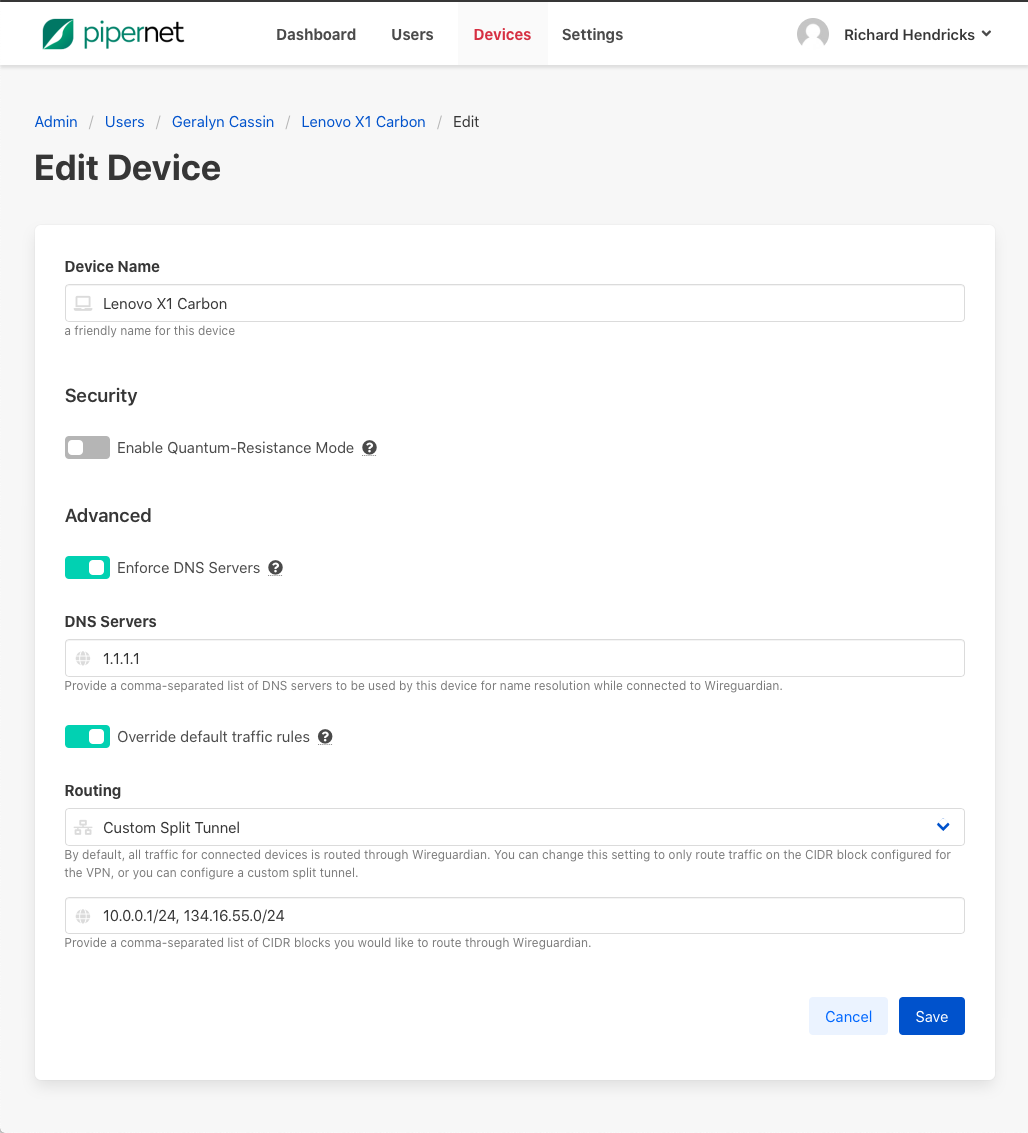
Administrators can override the server default traffic policy on a per-device basis to implement custom split-tunnel routes for privileged devices.
Security Fixes
Important: This release includes important security fixes for the base OS, application runtime and application dependencies.
| Package | Vulnerability ID | Severity | Status |
|---|---|---|---|
| ansi-html | CVE-2021-23424 | HIGH | |
| follow-redirects | CVE-2022-0155 | HIGH | |
| node-forge | CVE-2022-0122 | MEDIUM | |
| postcss | CVE-2021-23382 | MEDIUM |
To learn more about how to update your deployment to the latest version, please refer to our documentation.
Cover image by Jakob Søby on Unsplash
