Introduction
With our December release of KUY.io Konnect™ (v2112.0), we are thrilled to offer a new "quantum-resistance mode" switch for adding extra security to your most valuable VPN devices. Read on to see why that's a big deal and how you can use quantum-resistance mode today.
Background
Data networks play an essential role in our modern society: they bring people, enterprises, and nations together. Digital communication networks form the backbone of the modern society, similar to the way that power networks (meaning energy networks) were the backbone of the industrial society. So if they’re breached or compromised, the results can be grave!
Meanwhile, cybercrime continues to thrive: hardly a week passes without a cybersecurity incident making headline news across major media outlets. Rather than slowing down or stopping cybercrime, the pandemic ended up pouring gasoline on the fire, with many attacks directly related to work-from-home and hybrid workplace arrangements that caught business IT departments off guard and inadequately prepare to securely deal with.
As businesses accelerated the use of cloud, mobile and web applications, while at the same time transitioning away from on-premise networks and applications, risks of attack and network compromise increased manifold. Thus, businesses must explore every available avenue to better secure their networks, while making sure that their work-from-home and hybrid workforce stays productive, and engaged.
It's Time to Secure the Edge
Secure access service edge (SASE - pronounced "sassy") is an emerging cybersecurity concept and the latest trend when it comes to securing work-from-home and hybrid workforces. The core idea however has been around for a while. SASE combines networking and security functions in the cloud to deliver seamless, secure access to applications, anywhere users work. A secure access gateway in the cloud, like a KUY.io Konnect™ access server is a key component of an organization's overall secure edge strategy, together with a broader range of network security functions such as Web Filtering, Traffic inspection, IDS and malware filtering, as well as software defined networking that describes the allowed interconnections between nodes in the secure network.
Secure edge access is effective in protecting cloud services, networks, and the data and apps that run over them – from the corporate headquarters to users and their edge devices.
Yet, secure edge access has given rise to another network threat model that has become increasingly likely over the past 3 years. Now that businesses are increasingly securing the edge, threat actors are shifting their efforts towards "Harvest now, decrypt later" - storing up data for the day when more power powerful computers can break today's encryption algorithms.
History has shown us that encryption algorithms used to secure vital data across the world – from defense and banking to infrastructure and air travel - will be eventually be breached if enough time has passed by, and computing technology has exponentially grown to make the intractable possible. For example, OpenSSH in their 8.2 release noted:
It is now possible to perform chosen-prefix attacks against the SHA-1 hash algorithm for less than USD$50K. For this reason, we will be disabling the ssh-rsa public key signature algorithm that depends on SHA-1 by default.
As if you really needed another reason to switch from outdated VPN solutions using classical crypto such as IPSec, to a modern protocol like WireGuard®.
The Quantum Threat
Even though quantum computers won’t be available to the masses in the foreseeable future, tremendous research efforts from parties like Google, IBM, Honeywell, or D-Wave followed by Chinese universities and government sponsored companies are propelling quantum technologies forward at an unexpected rate.
Once available, quantum computing will be a game changer for security. The 54-qubit quantum chip unveiled by Google in 2019 completed a test computation in about 200 seconds. Today's most powerful supercomputer would have taken approximately 10,000 years to do the same. Recently, China has claimed to have produced a quantum computer, a million times faster than Google’s, capable of making a calculation in one millisecond that would take the world’s fastest super-computer 30 trillion years.
The security of many modern cryptographic methods relies on the fact that prime factorization of large numbers is not impossible, but it takes a very long time for classical computers to calculate: millions of years on your laptop; and this makes brute-forcing cryptographic keys unfeasible. Equipped with a quantum computer, it's possible to find the prime factors of a 2048-bit number in just minutes compared to the millions of years classical computers would take.
This is where attackers are hedging their bets with "harvest now, decrypt later attacks": they are betting that quantum computers will be able decrypt any network traffic protected with traditional cryptographic methods in the near future, and that some of the data has a shelf life beyond the time it will take to advance quantum computers to break the crypto used to protect the data.
As a modern business you need to start thinking about enhancing your defenses now. Even after quantum computers become mainstream, it will be quite a while before we see full quantum networks reaching to the edge. Therefore, businesses that choose to neglect quantum security are risking to be left defenseless when harvest now, decrypt later comes full-circle.
Protect your Edge Connections Today
KUY.io Konnect™ is not only extremely fast, but also secures your connection and protects your online privacy with several nice security features such as data security or identity-hiding. The underlying WireGuard® protocol works in two steps.
- First a handshake is performed between client and server. During this handshake, both participants authenticate both to each other and at the same time securely exchange key material.
- The key material is used to derive a symmetric key pair used to establish a secure tunnel for exchanging the actual network data. When using this tunnel a client can then “hide” behind the server and obtain additional privacy from other parties while connected to the VPN.
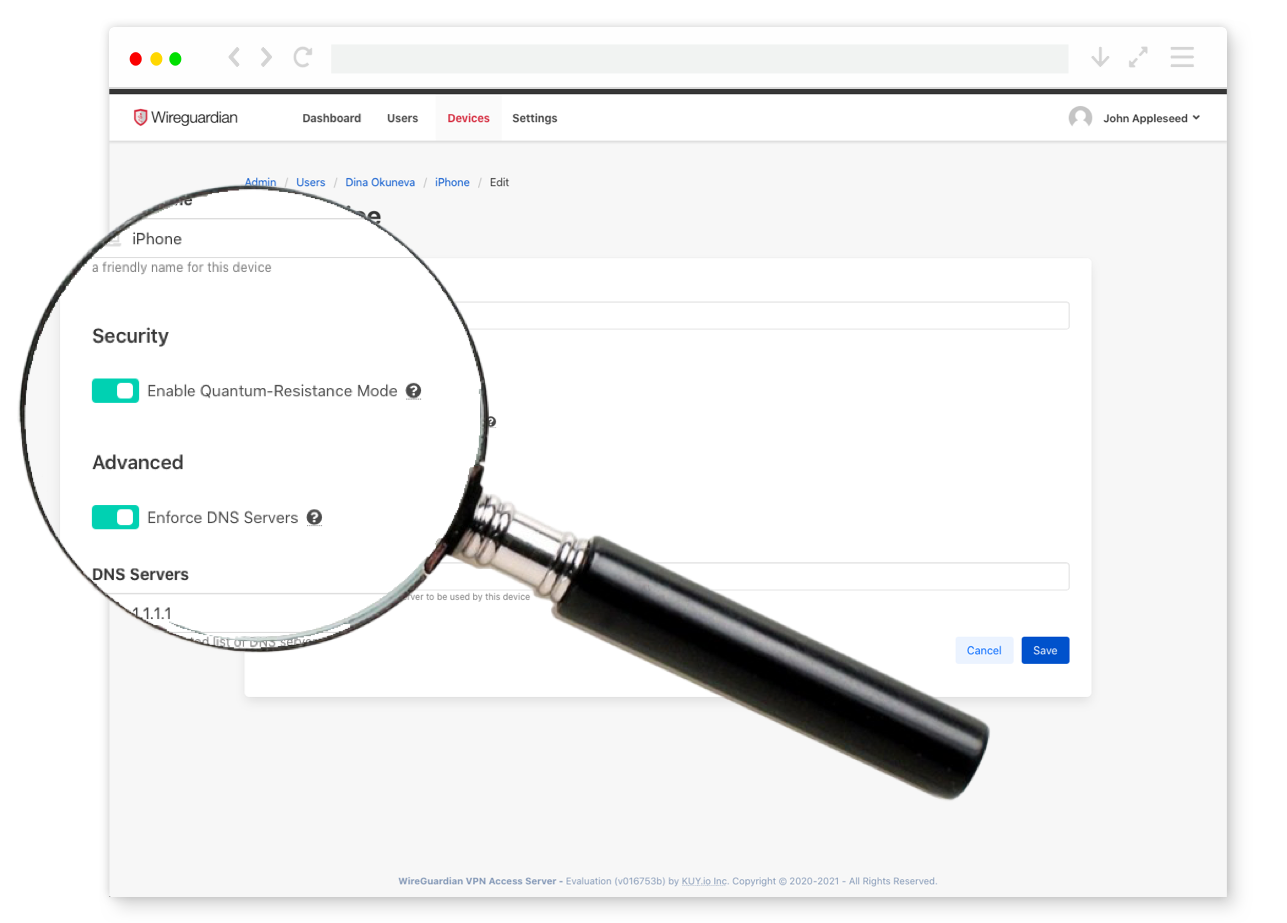
By enabling quantum-resistance mode in KUY.io Konnect™, you can protect your VPN traffic against harvest now, decrypt later attacks from future Quantum Computers.
By default the cryptography in use for the handshake, as modern as it is, is not quantum resistant and subject to the "harvest now, decrypt later" threat model explain above.
However, starting with our December release, your Konnect™ VPN can be made quantum resistant by simply turning on "quantum-resistance mode" when configuring your client devices. Under the hood, KUY.io Konnect™ access server will increase the key size by mixing in a special pre-shared key that adds quantum resistance to the server/device handshake.
While there are already proposals in the works for using post-quantum cryptography for securing VPN handshakes, the method used by the WireGuard® protocol is much more practical than that of competing protocols like OpenVPN. For example, Kudelski security reported that Post-Quantum crypto in OpenVPN required up to 1,200x the processing effort (CPU consumption resulting in power drain and heat) from the VPN client, and up to 2,000x the processing effort from the VPN server.
Takeaways
A secure connection gateway, such as KUY.io Konnect™ access server is a powerful tool to protect your edge network traffic, even after the advent of quantum computers. By turning on "quantum-resistance mode" you can bolster your edge network connection with an additional layer of protection against "harvest now, decrypt later" attacks in the future.
With our December release of KUY.io Konnect™ (v2112.0), we are making "quantum-resistance mode" available to all customers, regardless of whether you have a free or paid license. Merry Christmas!
.jpg?disposition=attachment)